When working with Azure Active Directory and multitenant applications users might get following error, when trying to logon.
| Additional information: AADSTS65005: The app needs access to a service ("https://yourdomainname.onmicrosoft.com/youraponame") that your organization "YOUR TENANT ID" has not subscribed to or enabled. Contact your IT Admin to review the configuration of your service subscriptions. |
To explain more precisely what caused this error, take a look on following picture:
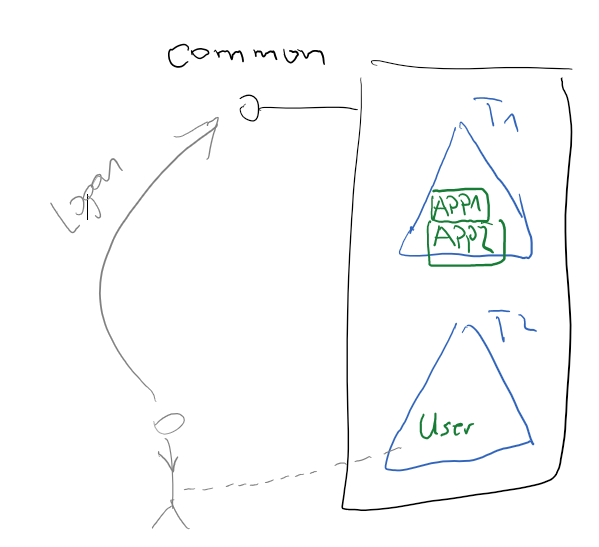
In this scenario there are two AAD tenants and two applications. Application APP1 is trying to access the application APP2 on behalf of user. Coincidently both applications are registered in the same tenant, but in a case of a Multifactor Application (MFA) this does not matter, because client application is obtaining tokens from /common endpoint (in MFA case).
AuthenticationContext ctx=new AuthenticationContext("https://login.windows.net/common");
In a none MFA scenario application would typically obtain the token from tenant’s endpoint:
AuthenticationContext ctx=
new AuthenticationContext(https://login.windows.net/TENANT-GUID);
Notice that user belongs to tenant, which does not own the application. This is very useful scenario, when you want to enable access to application in tenant1 from users registered in some other tenant. Before user can obtain the token, it is required to do complete following:
1. App1 (client) need a delegated permition to App2 (service)
2. App2 (service) has to register App1 (client) as known application.
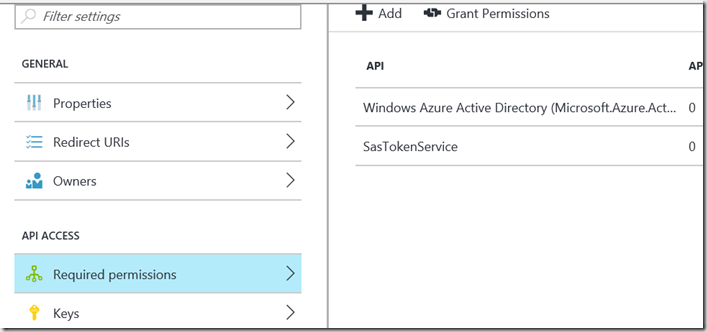
1. Add delegated permission
Go to registration of APP1 and permission to App2 (SasTokenService)
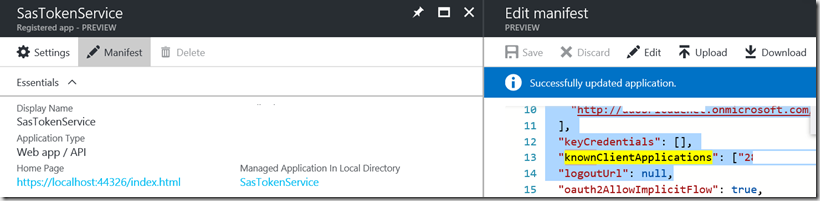
2. Add App2 to list of known applications of App2 (service)
Go to registration of App2, open its manifest and add it to list of known client applications as shown on picture below:
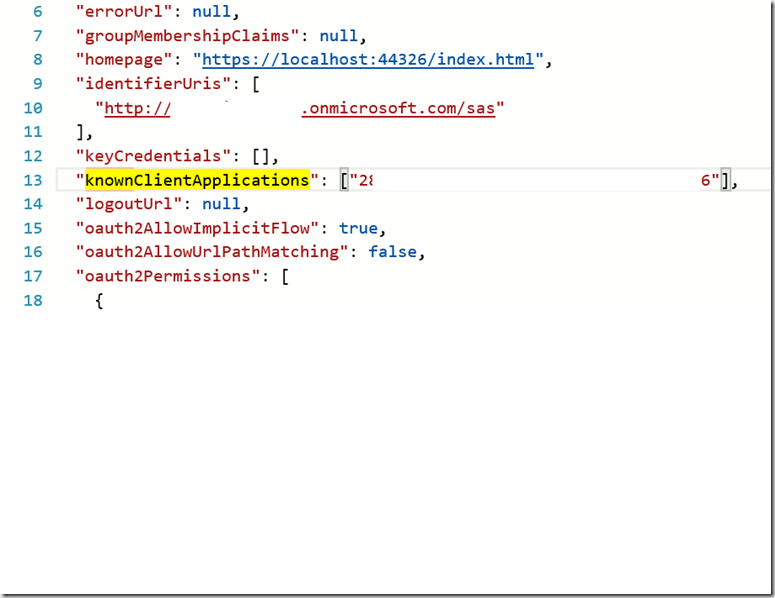
. . . manifest . . .
"http://***.onmicrosoft.com/sas" ],
"keyCredentials": [],
"knownClientApplications": ["***546"],
"logoutUrl": null,
. . .
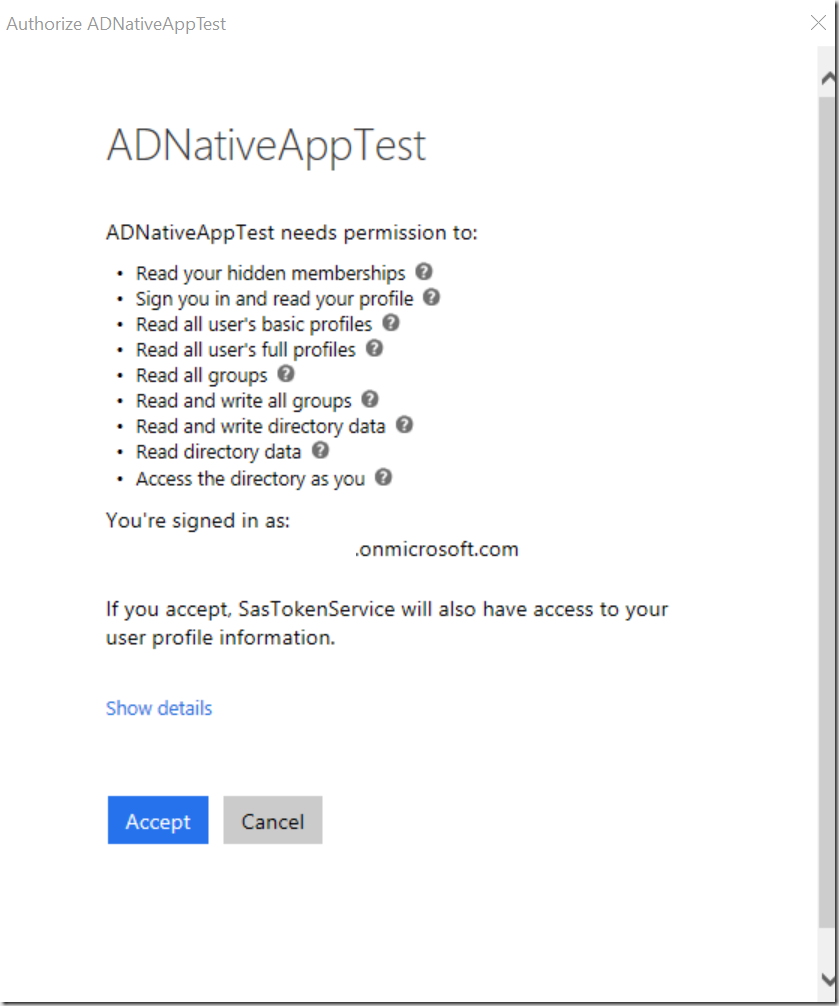
After all you will get consent dialog when trying to logon with a user, who belongs to tenant2.
Posted
Apr 11 2017, 10:59 PM
by
Damir Dobric