New operative systems are by default not very friendly to NTLM authentication. The introduce a set of group policies which control who can use NTLM in enterprise. Following picture shows the final configuration which I set up at my development machine:
![image_thumb[16] image_thumb[16]](http://developers.de/cfs-file.ashx/__key/CommunityServer.Blogs.Components.WeblogFiles/damir_5F00_dobric/image_5F00_thumb16_5F00_3763FA84.png)
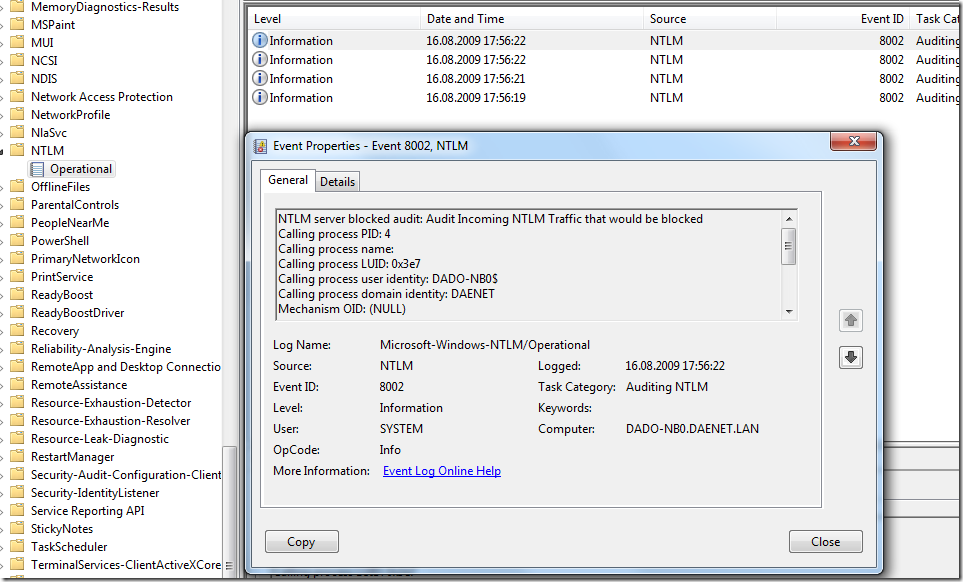
First of all I would recommend you enable auditing. This will give you enough information about hidden NTLM details. After you have configure them you can use NTLM event log for diagnostics:
Network security: Restrict NTLM: Audit Incoming NTLM Traffic
This policy setting allows you to audit incoming NTLM traffic.
If you select "Disable", or do not configure this policy setting, the server will not log events for incoming NTLM traffic.
If you select "Enable auditing for domain accounts", the server will log events for NTLM pass-through authentication requests that would be blocked when the "Network Security: Restrict NTLM: Incoming NTLM traffic" policy setting is set to the "Deny all domain accounts" option.
If you select "Enable auditing for all accounts", the server will log events for all NTLM authentication requests that would be blocked when the "Network Security: Restrict NTLM: Incoming NTLM traffic" policy setting is set to the "Deny all accounts" option.
This policy is supported on at least Windows 7 or Windows Server 2008 R2.
Note: Audit events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Network security: Restrict NTLM: Audit Incoming NTLM Traffic
This policy setting allows you to audit incoming NTLM traffic.
If you select "Disable", or do not configure this policy setting, the server will not log events for incoming NTLM traffic.
If you select "Enable auditing for domain accounts", the server will log events for NTLM pass-through authentication requests that would be blocked when the "Network Security: Restrict NTLM: Incoming NTLM traffic" policy setting is set to the "Deny all domain accounts" option.
If you select "Enable auditing for all accounts", the server will log events for all NTLM authentication requests that would be blocked when the "Network Security: Restrict NTLM: Incoming NTLM traffic" policy setting is set to the "Deny all accounts" option.
This policy is supported on at least Windows 7 or Windows Server 2008 R2.
Note: Audit events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Additionally to auditing policies there are few other restricting policies:
Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication
This policy setting allows you to create an exception list of remote servers to which clients are allowed to use NTLM authentication if the "Network Security: Restrict NTLM: Outgoing NTLM traffic to remote servers" policy setting is configured.
If you configure this policy setting, you can define a list of remote servers to which clients are allowed to use NTLM authentication.
If you do not configure this policy setting, no exceptions will be applied.
The naming format for servers on this exception list is the fully qualified domain name (FQDN) or NetBIOS server name used by the application, listed one per line. To ensure exceptions the name used by all applications needs to be in the list, and to ensure an exception is accurate, the server name should be listed in both naming formats . A single asterisk (*) can be used anywhere in the string as a wildcard character.
Network security: Restrict NTLM: Audit NTLM authentication in this domain
This policy setting allows you to audit NTLM authentication in a domain from this domain controller.
If you select "Disable" or do not configure this policy setting, the domain controller will not log events for NTLM authentication in this domain.
If you select "Enable for domain accounts to domain servers," the domain controller will log events for NTLM authentication logon attempts for domain accounts to domain servers when NTLM authentication would be denied because "Deny for domain accounts to domain servers" is selected in the "Network security: Restrict NTLM: NTLM authentication in this domain" policy setting.
If you select "Enable for domain accounts," the domain controller will log events for NTLM authentication logon attempts that use domain accounts when NTLM authentication would be denied because "Deny for domain accounts" is selected in the "Network security: Restrict NTLM: NTLM authentication in this domain" policy setting.
If you select "Enable for domain servers" the domain controller will log events for NTLM authentication requests to all servers in the domain when NTLM authentication would be denied because "Deny for domain servers" is selected in the "Network security: Restrict NTLM: NTLM authentication in this domain" policy setting.
If you select "Enable all" the domain controller will log events for NTLM pass-through authentication requests from its servers and for its accounts which would be denied because "Deny all" is selected in the "Network security: Restrict NTLM: NTLM authentication in this domain" policy setting.
This policy is supported on at least Windows Server 2008 R2.
Note: Audit events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Network security: Restrict NTLM: Incoming NTLM traffic
This policy setting allows you to deny or allow incoming NTLM traffic.
If you select "Allow all" or do not configure this policy setting, the server will allow all NTLM authentication requests.
If you select "Deny all domain accounts," the server will deny NTLM authentication requests for domain logon and display an NTLM blocked error, but allow local account logon.
If you select "Deny all accounts," the server will deny NTLM authentication requests from incoming traffic and display an NTLM blocked error.
This policy is supported on at least Windows 7 or Windows Server 2008 R2.
Note: Block events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Network security: Restrict NTLM: NTLM authentication in this domain
This policy setting allows you to deny or allow NTLM authentication within a domain from this domain controller. This policy does not affect interactive logon to this domain controller.
If you select "Disabled" or do not configure this policy setting, the domain controller will allow all NTLM pass-through authentication requests within the domain.
If you select "Deny for domain accounts to domain servers" the domain controller will deny all NTLM authentication logon attempts to all servers in the domain that are using domain accounts and return an NTLM blocked error unless the server name is on the exception list in the "Network security: Restrict NTLM: Add server exceptions for NTLM authentication in this domain" policy setting.
If you select "Deny for domain account" the domain controller will deny all NTLM authentication logon attempts from domain accounts and return an NTLM blocked error unless the server name is on the exception list in the "Network security: Restrict NTLM: Add server exceptions for NTLM authentication in this domain" policy setting.
If you select "Deny for domain servers" the domain controller will deny NTLM authentication requests to all servers in the domain and return an NTLM blocked error unless the server name is on the exception list in the "Network security: Restrict NTLM: Add server exceptions for NTLM authentication in this domain" policy setting.
If you select "Deny all," the domain controller will deny all NTLM pass-through authentication requests from its servers and for its accounts and return an NTLM blocked error unless the server name is on the exception list in the "Network security: Restrict NTLM: Add server exceptions for NTLM authentication in this domain" policy setting.
This policy is supported on at least Windows Server 2008 R2.
Note: Block events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
This policy setting allows you to deny or audit outgoing NTLM traffic from this Windows 7 or this Windows Server 2008 R2 computer to any Windows remote server.
If you select "Allow all" or do not configure this policy setting, the client computer can authenticate identities to a remote server by using NTLM authentication.
If you select "Audit all," the client computer logs an event for each NTLM authentication request to a remote server. This allows you to identify those servers receiving NTLM authentication requests from the client computer.
If you select "Deny all," the client computer cannot authenticate identities to a remote server by using NTLM authentication. You can use the "Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication" policy setting to define a list of remote servers to which clients are allowed to use NTLM authentication.
This policy is supported on at least Windows 7 or Windows Server 2008 R2.
Note: Audit and block events are recorded on this computer in the "Operational" Log located under the Applications and Services Log/Microsoft/Windows/NTLM.
Posted
Aug 16 2009, 08:04 PM
by
Damir Dobric